Role of AI for cybersecurity in electronic supply chain
The demand of increasingly intelligent products is rising in virtually all industry segments. This growth will continue to grow across the industry from fortune 500 to start-ups to unlock newer and better products. It is estimated that by 2030 almost 50 billion products will be installed around the world. As the cyber physical systems and IoT market is hinting to hit the trillion-dollar mark, Electronic OEMs are forced to manufacture and assemble components globally to be cost competitive. Untrusted third-party entities like vendors, foundries, service stations can potentially exploit this opportunity to introduce counterfeits, malicious chips, trojans that serve as backdoor entries to access sensitive data or side channel attacks that could potentially alter the functioning of the chip altogether. Vulnerabilities of ICs and presence of unknown added malware circuitry has led to unexplained military mishaps. The FBI, U.S. Immigration and Customs Enforcement (ICE), and U.S. Customs and Border Protection (CBP) kicked off an international initiative to control the illegal supply of fake network hardware. Between 2005 and 2010, they seized nearly $143 million worth of counterfeit hardware.
A typical hardware trojan consists of a payload and a trigger. The payload is usually hidden or masked inside the dense PCB and may get neglected in the AOI tolerances. The payload can be smaller than a tip of a sharpened pencil (as example shown in Figure 1). Our group is working on proposing novel techniques to detect any alterations made to the designed printed circuit boards (PCB) using artificial intelligence (AI) tools like image processing and deep learning. The overall functioning would be based upon building a deep classifier. (Fig 2) Deep network allows deeper penetrations and have performed very well on other image recognition tasks. (Fig 4)
With our proposed solutions we can potentially detect PCB level attacks like alterations made to the gates, hidden chips, counterfeits based on semi supervised learning. This combined with side channel signal analysis, and reverse engineering the potential trojan could significantly reduce the threat of leaks in sensitive data, bypasses made to gates.

Fig 1: Size of the malicious chips in comparison with a penny |
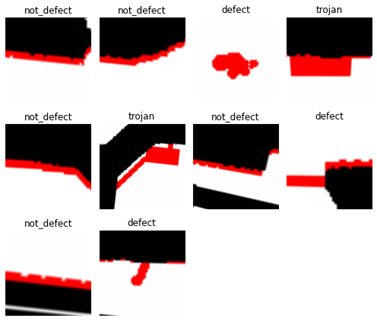
Fig 2: Labelled training data. |

Fig 3: Image processing. |

Fig 4: Deep residual network (ResNet34) Architecture used for object recognition. |
| Table 1: 34 layer residual network. building blocks are shown in brackets. | ||
| Layer name | Output Size | 34 Layer |
| Conv_1 | 112×112 | 7×7, 64, stride 2 |
| Conv_2 | 56×56 | 3×3 Max pool, stride 2 |
| Conv_3 | 28×28 | |
| Conv_4 | 14×14 | |
| Conv_5 | 7×7 | |
| 1×1 | 1×1 | average pool, 1000-d fc, softmax |
| FLOPs | ||